Cyber security: what stands behind cyber-threats and how to avoid them?
Every now and then groups of experienced cybercriminals gain control over other people’s computers and gadgets by implementing series of programs that destroy particular websites. In a blink of an eye these programs shutdown ATM stations, companies, phone lines, and even governmental websites of different countries. That is why many countries spend a lot of time and money to look more attentively at cybersecurity and control informational resources.
Amidst these escalating cyber threats, the concept of Privacy Defend emerges as a crucial shield for individuals navigating the digital landscape. Privacy Defend, an intrinsic aspect of contemporary cybersecurity efforts, signifies the collective commitment to safeguarding online privacy and fortifying defenses against malicious activities that jeopardize the integrity of personal and organizational data.
Lately, one of the world leaders in informational technologies, Cisco released its 10th annual report on informational security where it analyzed the latest news about threats and the current situation in the informational security field.
Senior vice-president and executive director of the company working in informational security John Stuart claimed, “In 2017, cyber-space is a business and businesses run in cyber-space, and it requires a completely different approach and different results. One needs to be always developing and this development should be estimated regarding effectiveness, costs, and wisely thought-of risks. Report on informational security shows and, I hope, grounds our answers to problems of budget, staff, innovations, and architecture.” Just as cybersecurity needs a dynamic approach, so too does the online entertainment industry. This is exemplified by businesses like casino trực tuyến, which must continually evolve to address cybersecurity threats while offering secure and innovative gaming experiences to their users.
A little less than 3000 informational security directors and heads of IS departments from all around the world took part in the research.
According to the research more than a third of the organizations who have had their informational systems hacked in 2016 spoke about significant (more than 20%) losses of income, lost opportunities, and the outflow of customers. Most of these organizations, after such attacks, looked deeper into technologies which can protect them from threats, started dividing functions of IT, and the for the departments that provided informational security, started intensifying trainings and implementing methods for cutting the risks.
As with over a third of surveyed organizations reporting substantial losses and disruptions due to cyber-attacks, the focus on protecting informational systems extends beyond traditional measures. App security, and particularly pentesting, emerges as a critical component in this evolving strategy. As organizations intensify their efforts to safeguard against threats, penetration testing(pentesting) serves as a proactive measure, allowing them to identify and address vulnerabilities within their applications. By investing in app security measures like penetration testing, businesses aim to fortify their defenses, mitigate risks, and ensure the resilience of their informational infrastructure in the ever-evolving landscape of cyber threats.

Executives of the companies who are responsible for informational security named lack of resources, incompatibility of informational security systems, and lack of qualified professionals among their most important barriers from promoting the main principles of informational security. In addition, directors said that 65% of organizations use from six to 50 or more systems of cybersecurity and this, as experts claim, contributes to development of new gaps in security.
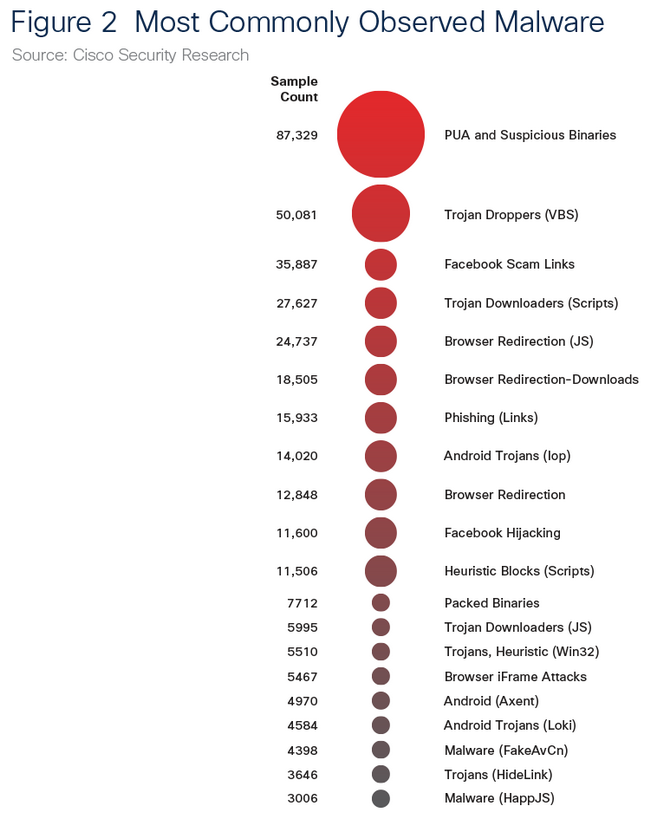
Report tells that hackers use these gaps and return to “past attacks” kept in pilot versions of software and mail spam. It should be added that statistics on spam quantity amaze—almost two thirds (65%) of messages are considered spam and 10% of them are regarded as dangerous. This already existed in 2010. In addition, more and more spam is being received from big botnets.
Cost of cyber-threats for businesses: lost customers and decreased income
In the report, Cisco showed the potential connection between cyberattacks and the company’s condition. Cyberattacks resulted in the following:
- 22% of organizations, which were attacked, have had the quantity of their clients reduced; moreover 40% of them have had the number of their customers decrease by 20%
- 29% had their income significantly reduced, 36% of them had their income decline by 20%
- 23% of affected companies have reported about loss of profit, 42% of them have lost more than 20% of beneficial offers.
Cyber-attacks and new “business-models”
Last year we saw the creation of a new hackers’ tendency—cyber-groupings became more “corporate.”
Criminals use old, proven technical methods, just like before, but together with that, now such methods create new opportunities.
- New methods that hackers create often look more and more like corporate hierarchy. Many organizations use so-called brokers or “floodgates” which work as middle management and mask malicious activity. They help criminals because it allows them to accelerate their actions, take control over software space, and avoid detection
- Usual adware, which sends advertisements without notifying users, shows its effectiveness over and over: more than 75% of studied organizations are infected by it.
- The great news was the reduced popularity of such large sets of exploits as Angler, Nuclear, and Neutrino, the activity of which was prevented in 2016 but smaller players quickly took their places.
How can you minimize the risks of cyberattacks
For minimizing risks experts advise the following:
- The question of providing informational security should be one of the most important business-priorities. Security has to become a daily question for executives.
- Research on operational disciplines. What should be also be revised is existing security, adjustments of software, control over the access to networks, apps, functions, and data.
- Testing the effectiveness of the security.
- Systematic approach to the security. Integration and automation should be placed at the top of all security criteria. Systematic approach will let you better control and improve mutual compatibility and reduce the amount of time spent on detection and prevention of cyberattacks.
The development of technologies results in development of cyber-attacks’ methods but at the same time lets you protect from them more effectively. The most important part of this is a strong security base. Modern underground economy makes cybercrime a kind of business, and to commit this crime it is not essential to have any extra knowledge. Criminals can be whoever they want and live wherever they want. It is enough to just buy one of the exploits package.
As you can see from this article, the most important thing in prevention of cyber-attacks is paying attention to security and taking seriously any (even small) changes or malfunctions in the system in general or its particular parts.